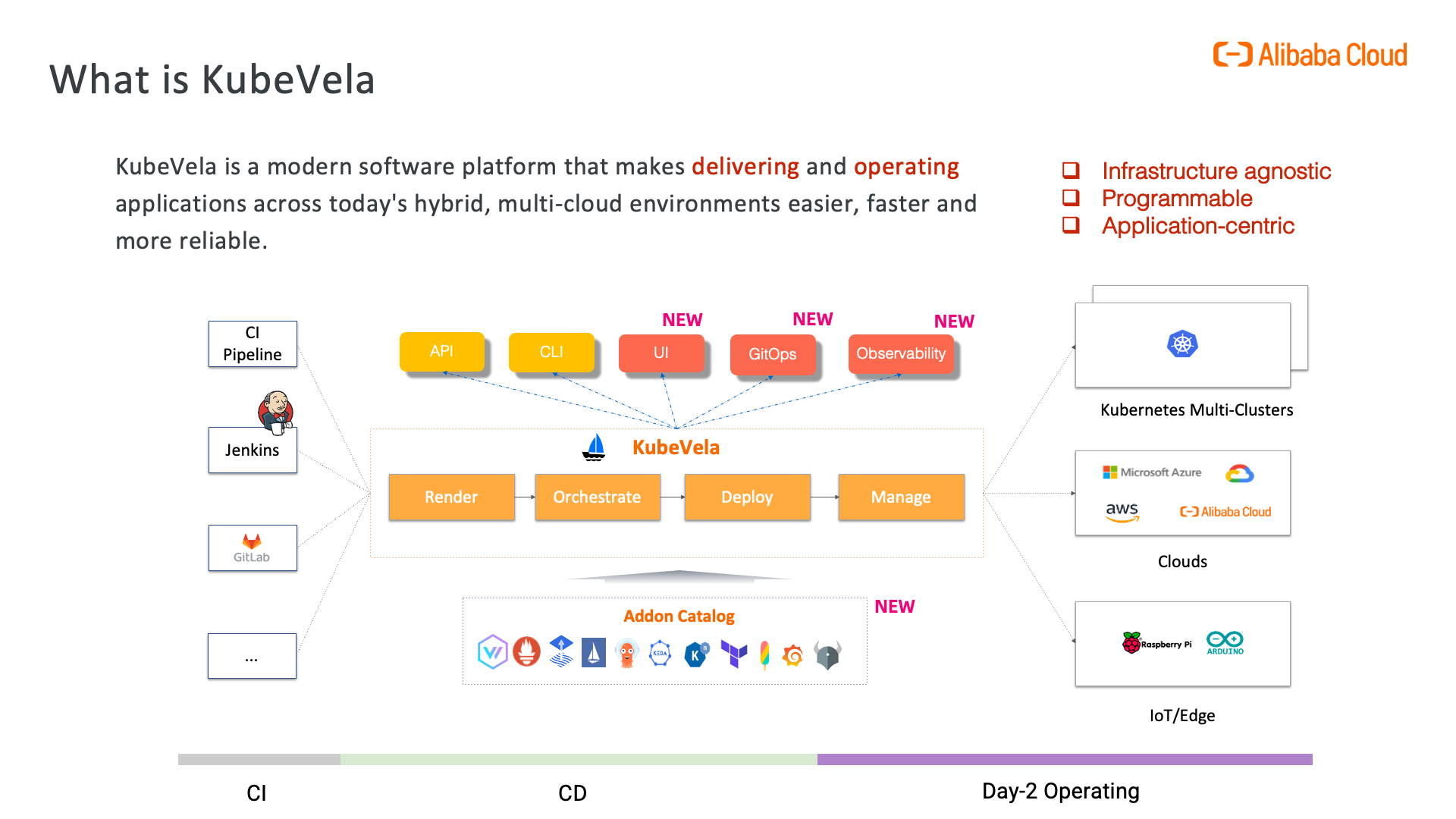
KubeVela 1.10.4 Now Available
Hello community! 👋
This is the first blog post in a while but we are excited to reinvigorate the community and keep developers and users up to date with all things KubeVela. The team is committed to providing regular updates, news and information about upcoming events and features.
We recently released the latest v1.10.4 which includes a host of useful features to improve the maintainability of Applications deployed with Kubevela. This blog will provide a quick overview of the features and how you can get started with utilising them in your KubeVela setup.
While v1.10.4 follows semantic versioning as a patch release, we're excited to deliver several new opt-in features alongside the usual bug fixes and improvements.
These features are disabled by default (where applicable) to maintain backward compatibility, allowing users to adopt them at their own pace.